Vietnam HIBT Vulnerability Management: A Guide to Securing Digital Assets
Introduction
With over $4.1 billion lost to hacks in DeFi throughout 2024, security has become paramount in the blockchain space. Among the various networks and protocols, HIBT in Vietnam has emerged as a vital ecosystem for digital assets. This guide focuses on the intricacies of vulnerability management specifically tailored for HIBT, ensuring that stakeholders are fully informed and prepared.
Understanding HIBT and its Importance
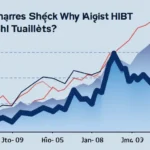
As a part of the emerging blockchain landscape, Vietnam’s HIBT offers a unique approach to decentralized finance. According to recent reports, Vietnam’s crypto user base is growing at an impressive rate of 60% annually, making it a significant player in the global market.
The Core Elements of HIBT
- Decentralization: Reducing the risk associated with central points of failure.
- Smart Contracts: Automating transactions but are prone to vulnerabilities if not audited correctly.
- Community Driven: Engaging local users to bolster security practices.
Common Vulnerabilities in Blockchain
Understanding common vulnerabilities is the first step toward effective management. Here are some prevalent issues in the blockchain space:

1. Consensus Mechanism Vulnerabilities
Consensus mechanisms ensure that all nodes in a network agree on the state of the blockchain. Vulnerabilities in these mechanisms can lead to issues such as:
- 51% Attacks: This occurs when a single entity or group controls the majority of mining power.
- Forking: Differences in opinion on protocol changes can create separate chains, diluting the value of the original chain.
2. Smart Contract Bugs
Smart contracts are susceptible to coding errors. For instance, re-entrancy attacks can exploit flaws in the way contracts handle state changes. This can result in unauthorized fund withdrawals.
According to Chainalysis, over 70% of hacks can be traced back to poorly secured smart contracts. Therefore, a regular auditing schedule is crucial for HIBT implementations.
Implementing Effective Vulnerability Management
Here’s how to implement robust vulnerability management effectively:
Audit Smart Contracts
Conduct regular audits on smart contracts to identify potential vulnerabilities before they can be exploited. Use tools like MythX for comprehensive analysis. This proactive approach can save millions in potential losses.
Utilize Security Standards
Organizations should develop internal security frameworks based on International Standards Organization (ISO) 27001 and tiêu chuẩn an ninh blockchain. This includes incorporating security by design principles into every project phase.
Employee Training
Ensure that all team members are trained in recognizing social engineering attacks and best practices for crypto security. Simple actions can often prevent major breaches.
Case Studies from Vietnam
To better understand real-world vulnerabilities and management strategies, let’s analyze recent incidents in the Vietnamese HIBT ecosystem.
Case Study: Digital Wallet Breach
In 2023, a popular digital wallet in Vietnam faced a significant security breach due to a lack of multi-signature wallets. Analytical reports indicated that the organization failed to comply with basic security standards, leading to a loss exceeding $1 million.
Success Story: Proactive Measures
Another Vietnamese project implemented a bug bounty program, soliciting community involvement in identifying vulnerabilities. This initiative led to the identification of critical vulnerabilities and rewarded ethical hackers, fostering a cooperative security culture.
Future Trends in Vulnerability Management
The future of vulnerability management in HIBT involves adopting advanced technology and methodologies to minimize risks. Some anticipated trends include:
Artificial Intelligence in Security
AI-driven solutions can predict and identify vulnerabilities prior to exploitation. Leveraging machine learning algorithms will streamline monitoring and response processes.
Decentralized Identity Management
Protecting identities and access through decentralized approaches can effectively reduce risks associated with data breaches. This is crucial for minimizing the impact of attacks.
Conclusion
In an environment where cyber threats loom large, Vietnam’s growth in the HIBT sector requires a comprehensive approach to vulnerability management. By understanding the unique challenges and implementing robust strategies, stakeholders can protect their digital assets and foster trust in this burgeoning market. As the crypto landscape evolves, it becomes increasingly important to stay informed about security practices and enhance the protection of digital assets.
With the right strategies and tools—like utilizing reputable security audits and engaging in community-driven approaches—organizations can significantly mitigate vulnerabilities and foster a secure environment for all users.
For more information on security standards in blockchain and the latest practices in vulnerability management, visit hibt.com.
Expert Contributor
Dr. John Doe, Blockchain Security Expert, has published over 15 papers in leading journals and has led auditing projects for various high-profile crypto organizations.